Though threats to cybersecurity bombard us in the news, imagine if a slip-up on your work computer takes down the entire Selkirk College system! It’s a real possibility.
Cyber security refers to protecting systems connected to the internet from threats in cyberspace. It involves protecting software, data, and hardware and helps prevent cybercriminals from gaining access to devices or the networks.
IT Services at Selkirk College want to help you stay safe from hackers and phishing attacks. Check out the topics below to find answers to some common questions or situations you may experience.
Remember to Stop and Think before you Click!
Phishing
Phishing is a form of fraud in which the attacker tries to learn information such as login credentials or account information by masquerading as a reputable entity or person.
Targeted attacks typically start with a phishing email sent to as many people as possible, that contains a link to a malicious website. It can often appear to come from a trusted source.
After clicking on the link, the attacker will attempt to infect and take control over the victims’ computers or harvest their usernames and passwords.
Phishing attempts are becoming more and more sophisticated these days and our personal information is highly at risk.
Selkirk College is also at risk because our systems store highly confidential data such as SIN numbers, banking information (such as direct deposit), health information, student data, etc.
Cyber criminals use phishing because it's easy, cheap and effective. Email addresses are easy to obtain, and emails are virtually free to send. Those who fall for phishing scams may end up with malware infections (including ransomware), identity theft, and data loss.
If you receive what you think is a phishing message, you can either:
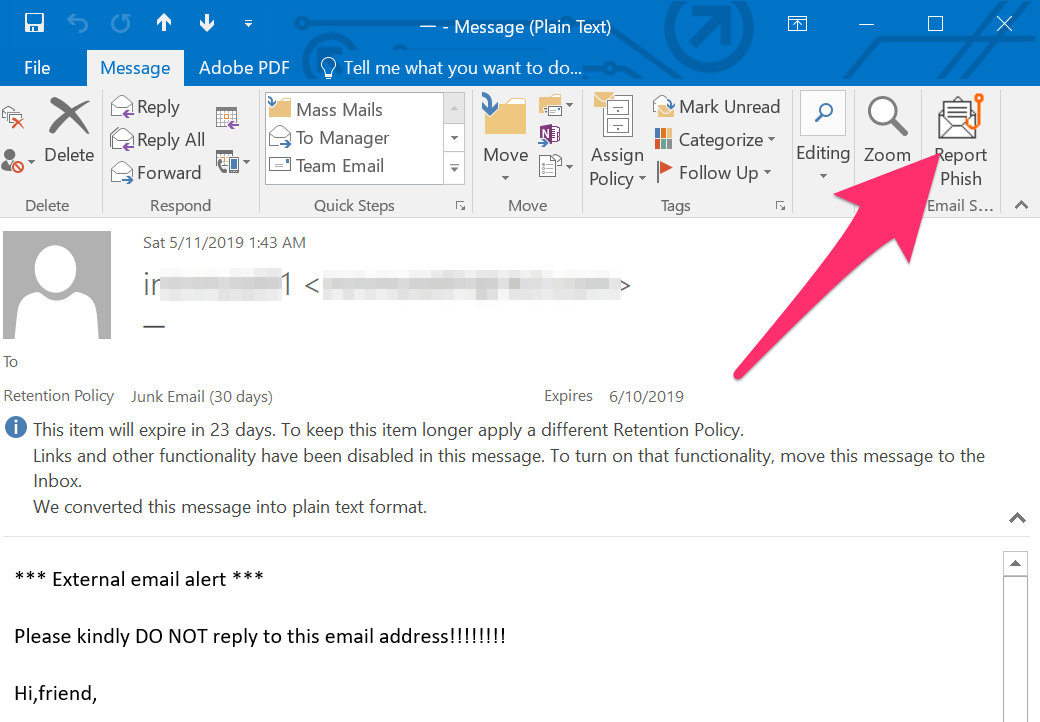
Use the 'Report Phishing' button in the Outlook Client to report the email and automatically delete it. If you use Outlook on the Web, click on the Junk tab and then Phishing.
 |
|
|---|
- Submit an IT Services ticket an include the suspicious email as an attachment. An IT team member can view and access the email and follow up if necessary.
- Delete the email if you’re pretty sure it’s a phishing message and you don’t have time to deal with it.
Check with a friend or colleague first to see if they received the same email.
- Do not forward to any other email address.
- Do not forward to IT Helpdesk as a ticket. (Just use the Outlook "report phishing button".
- Do not open or click attachments or links.

When you report and email as phishing, the email is moved to your Deleted Items folder. If you accidentally hit the report phishing button, don't worry, you can un-delete the email and it will move back into your inbox.
Visit https://passwords.selkirk.ca and change your password immediately!
For additional assistance or information, contact the IT Helpdesk via ticket, Zoom or phone.
Phone Support: Ext. 55255
Toll free 1-844-304-6500
- Do not click on links in messages. Hackers will create fake links to send you to a malicious website. Simply viewing the website can allow an attack on your system.
- Do not provide personal information about anyone to any organization or person online.
- Do not enter your personal information in a pop-up window.
- Do not send sensitive information via email.

1. The email is sent from a public domain.
No legitimate organization will send you an email from an address ending with '@gmail.com.' No! Not even Google.
Almost all organizations have their own email domain and company accounts from where they send out official messages. Therefore, before opening an email, ensure that the domain name (what follows after @) matches the sender. There is a catch, though. Hackers may try to mimic a real email. For example, if an address looks like 'paypal@notice-access-273.com', that is a red flag.
A genuine email from PayPal will have PayPal in the domain name, i.e., after the @ symbol.
2. The email requests your sensitive information.
If you receive an anonymous email asking for sensitive information, chances are it's a scam. No companies will send you an email requesting passwords, credit card data, SIN, nor will they send you a login link.
3. The email has terrible grammar.
Bad grammar is one of the easiest ways to recognize a phishing email. Because the legitimate ones are always well-written with no lousy syntax, they are often written by professional writers who exhaustively check for spelling before sending them out.
So, the next time you receive an email with strange phrases and poor language in the body of the message, it is most likely a phish.
4. The email has a suspicious attachment.
You should be alarmed if you receive an email containing an attachment from a company that you do not recognize or that you weren't expecting. A malicious URL or trojan may be included in the attachment.
It's good practice always to scan it using antivirus software first, even if you believe the attachment is real.
5. The message has made you panic.
Phishing emails are popular to incite fear in the recipient. The email can say that your account may have been compromised, and entering your login details is the only way to verify it. Alternatively, the email will state that your account will be closed if you do not respond immediately.
In any case, contact the company through other methods before committing any action.

6. The email says you have won a lottery.
So, you received an email about winning a lottery, gift cards, or some new gadgets, but you do not remember buying tickets for it—that's definitely a scam.
And when you open the message and click on a link, you will be redirected to a malicious website.
7. The email is from a government agency.
The government will never contact you directly. And most definitely, they won't engage in email-based harassment. Scammers send messages to victims claiming to be Revenue Canada or the RCMP demanding their personal information.
Revenue Canada sends direct official letters to home addresses and do not send you an email or call you until you receive an official letter.
Selkirk College employs the following methods to reduce phishing spam on campus:
- Built in spam filter rules via Outlook email
- Windows Defender: Antivirus protection
By employing these methods, Selkirk College filters approximately 1500 fraudulent emails per day.
Reply-Chain Attacks on Email
Reply-Chain attacks on emails with HTML attachments are on the rise in Post-Secondary Institutions.
Reply-chain email attacks are targeted phishing attacks in which the hackers gain access to ongoing business email thread conversations and plant disguised malicious links or attachments there.

Ordinary phishing attacks, usually have red flags such as grammar or spelling errors. However, reply-chain attacks are more sophisticated and are carefully-crafted with no language errors.
- Since reply-chain attacks rely on account compromises, be sure to follow best practices for security which include 2FA, use a unique password or passphrase, and check your email client settings and rules to make sure messages are not unknowingly being diverted or deleted.
- Knowledge is Power! Engage in Security Awareness Training and stay current on Cybersecurity issues.
- Always pay attention to attachments, even if they are from a known source.
Password Security
Passwords are intended to ensure that only authorized individuals are permitted access to your computer system and your data. They secure computers against potential assaults from the cybercriminals who break into systems and steal identities to commit crimes.
Passwords or Paraphrases should be:
- kept confidential
- 10-15 characters in length with a symbol and number
- never shared with anyone, or use in plain sight of others
- changed frequently (3-6 months)
- unique for each system you log into
Weak passwords welcome hackers!
A common name, such as your name or the name of your pet
Your ID or part thereof–in any sequence
Your address or date of birth
Old passwords with one or two characters changed
Strong Passwords = Strong locks
Secure passwords or passphrases should be a minimum of 8 characters in length, contain upper and lower case letters, numbers and symbols. Avoid the obvious and the predictable. Start with something only you know and will remember.
- Use the first letters of words in a easily memorized sentences or phrases
- Use random combinations of alphabetic characters, numbers and special characters
- Insert silent characters into words or double words EG. choc9ola7te
- Use numbers and letters that create a sentence EG.4warned_4armed
For the sake of convenience, many people who put strong locks on their front door often still hide a spare key under the doormat.
Likewise, many people who have difficulty remembering their passwords often opt for the equivalent of the key under the doormat strategy by:
- Formulating weak passwords that are easy to crack;
- Hiding their passwords in obvious and accessible places where anyone could easily find them, such as taped to the bottom of their keyboard or adjacent desk drawer; or,
- Never changing their passwords because devising and remembering new passwords is too much trouble.
Ideally, you should commit your passwords to memory; but if you find this difficult, here are two practical suggestions:
- Consider installing an application such as KeePass, Pretty Good Privacy (PGP) or GNU Privacy Guard (GnuPG) which secures your list of passwords with a common password.
- As a last resort, write down your passwords, put them in a sealed envelope and hide it where only you know where to find it.
Email Security
The Safe Senders list in Outlook lets you control which emails don't land in the Junk Email folder.
Outlook Client
- On the Home tab, click Junk, then click Junk E-mail Options.
- On the Safe Senders tab, select the Add button, type in the email and click on OK then Apply.
Outlook on the Web
- Go to Settings.
- At the bottom of the pane, click View all outlook settings.
- In the left pane, select Mail> Junk Email
- Under Safe Senders and Recipients, select +Add enter the email address or domain you want to add then hit Enter on your keyboard.
- Select Save
Messages end up in quarantine because they were classified as malware, spam, phishing, or bulk. Users can review their quarantined messages within 30 days of the received date and chose if you want to block sender, release, review or delete the message. Click on the following link to view your quarantined messages: https://security.microsoft.com/quarantine

Phishing emails are more and more frequent these days, especially near the holidays. Hackers are very tricky and phishing emails can be hard to recognize. If you accidentally click on a link within a phishing email, do the following:
- Disconnect your device from the internet, close all programs and shut down your computer.
- Contact IT Services to report the incident.
Cybersecurity Myths
Cybersecurity is a highly technical process that only your IT department can handle.
The security tools that your IT department manages are important, but technology can only do so much. These security measures can’t stop an employee from sending sensitive information within an email. Creating a human firewall, made up of each and every employee, is essential to the security of your organization. Security is everyone’s responsibility.
High-tech hackers pose the highest threat to your organization.
You may imagine a cyberattack as the use of highly sophisticated technology to break down firewalls and decode user passwords. But in truth, it is much more likely that Dave wrote his password on a sticky note and it fell into the wrong hands. Human error is an easy target for cybercriminals, so stay alert!

High-tech hackers pose the highest threat to your organization.
You may imagine a cyberattack as the use of highly sophisticated technology to break down firewalls and decode user passwords. But in truth, it is much more likely that Dave wrote his password on a sticky note and it fell into the wrong hands. Human error is an easy target for cybercriminals, so stay alert!
Security awareness only really matters when you’re at work.
Your organization’s at-work policies and compliance regulations may not be necessary in your home life, but security awareness still matters. Scammers could phish your personal email for bank accounts, login credentials, or even personally identifiable information, which can be used to perform identity theft.
Smart devices are rarely targeted by cybercriminals.
Nearly everyone has a smartphone and many people use smart devices throughout their homes. From smart speakers to security cameras to lightbulbs, all of these gadgets connect to the internet. As these devices become the norm, cybercriminals happily accommodate. Treat smart devices the same way you would treat any other computer. Always use strong passwords, install antivirus and anti-malware software, and keep these devices up-to-date with the latest security patches.
Training and Resources
Take the time to expand your cybersecurity knowledge and learn more about safe online practices you can incorporate into your daily life. Build your cyber score while completing online learning modules through KnowBE4.
KnowBE4 - every employee has access to short, interactive cybersecurity training videos via the KnowBE4 platform. Login to your Knowbe4 dashboard to access a variety of training modules. If you want specific cybersecurity training, contact IT Services to see what's available.
Additional Resources:
- Get Cybersafe - Tips for Kids and Families: https://www.getcybersafe.gc.ca/en/blogs/key-cyber-security-topics-kids-need-know-about
Government of Canada: https://www.getcybersafe.gc.ca/en
Government of Canada: https://cyber.gc.ca/en/learning-hub